Researchers have provided the details of an investigation into cyberattacker activity linked to DarkSide ransomware.
On Tuesday, FireEye researchers documented five separate clusters of activity suspected of being connected to DarkSide, the Ransomware-as-a-Service (RaaS) network responsible for the Colonial Pipeline security incident.
Colonial Pipeline, one of the largest fuel pipeline operators and delivery companies in the United States, suffered a ransomware outbreak last week which has resulted in pipeline closures and fuel shortages. The firm is yet to restore all of its systems and the case -- as it involves a critical infrastructure (CI) asset -- is deemed serious enough to involve the FBI.
DarkSide's core team has attempted to distance itself from the attack by claiming to be "apolitical" and a group simply in it for the money. However, the incident has prompted the interest of not only law enforcement, but security researchers tracking RaaS services.
So far, FireEye has tracked five threat actors who are either current or past DarkSide RaaS affiliates.
RaaS subscribers are given access to custom malware -- in this case, the DarkSide ransomware variant -- in return for developers receiving a slice of any ransom payment profits.
Forum posts indicate that affiliation requires 25% of the cut for ransom payments under $500,000 and this is decreased to 10% for anything over $5 million.
According to the researchers, anyone who tries to join the DarkSide RaaS group has to pass an interview, and if they succeed, are then provided with a control panel for selecting their ransomware build, managing their victims, and contacting support.
In addition, users can specify what information, stolen during a cyberattack, can be published on the main DarkSide leak site. This is known as a double-extortion tactic in which companies that refuse to pay for a decryption key are then threatened with the public leak of their files.
FireEye has described the current activities of three out of the five linked groups, tracked as UNC2628, UNC2659, and UNC2465.
UNC2628: This group has been active since February. They tend to move quickly from initial infection to ransomware deployment and may only lurk on a compromised network for two to three days before starting encryption.
Suspicious authentication attempts, brute force attacks, and 'spray and pray' tactics are common, and this threat actor may also acquire initial access through legitimate credentials for corporate virtual private networks (VPNs), which can be purchased from other cybercriminals online.
UNC2628 is thought to partner with other RaaS services including REvil and Netwalker.
UNC2659: The second cluster, active since at least January, moves from initial access to ransomware deployment in an average of 10 days.
This set exploits CVE-2021-20016 to obtain initial access, a now-patched vulnerability in the SonicWall SMA100 SSL VPN, a service designed for mobile workers.
"There is some evidence to suggest the threat actor may have used the vulnerability to disable multi-factor authentication options on the SonicWall VPN, although this has not been confirmed," FireEye says.
TeamViewer is abused to maintain persistence on a compromised machine and the group exfiltrates files before encryption.
UNC2465: With cybercriminal activity dating back to at least April 2019, UNC2465 now uses phishing emails to deliver DarkSide via the Smokedham .NET backdoor. In a case documented by FireEye, initial access to a network was obtained months ahead of ransomware execution.
Smokedham also supports the execution of arbitrary .NET commands, keylogging, and screenshot generation. The NGROK utility is used by the threat actors to circumvent firewalls and expose remote desktop service ports.
In related news, Sophos has been called in to assist on five different instances of DarkSide ransomware infection. The company has reported an average time of 45 days between initial access and ransomware deployment. A copy of the typical ransomware note is below.
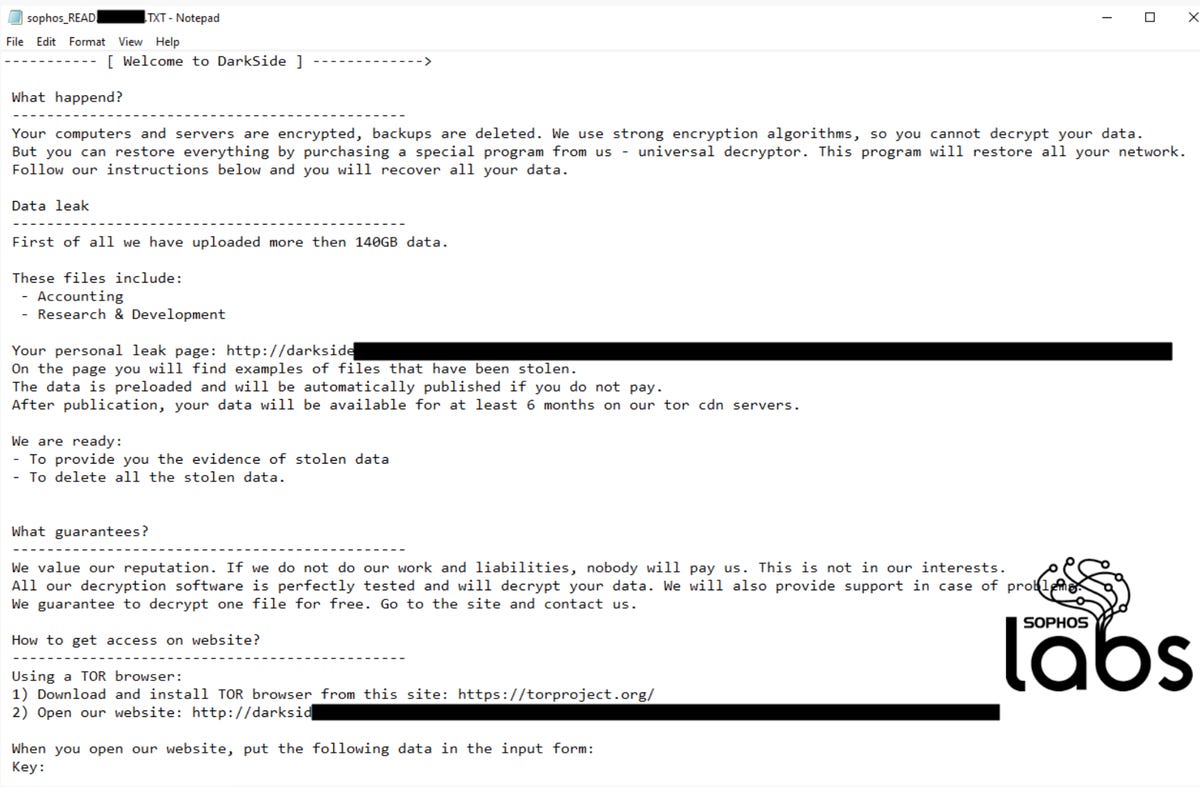
"We believe that threat actors have become more proficient at conducting multifaceted extortion operations and that this success has directly contributed to the rapid increase in the number of high-impact ransomware incidents over the past few years," FireEye commented. "We expect that the extortion tactics that threat actors use to pressure victims will continue to evolve throughout 2021."
Previous and related coverage
Have a tip? Get in touch securely via WhatsApp | Signal at +447713 025 499, or over at Keybase: charlie0
"five" - Google News
May 12, 2021 at 06:00PM
https://ift.tt/3uJnblj
Researchers track down five affiliates of DarkSide ransomware service - ZDNet
"five" - Google News
https://ift.tt/2YnPDf8
https://ift.tt/2SxXq6o
No comments:
Post a Comment